Why Are People So Obsessed With Humanoid Robots?
Humanoid robots have been a long-lasting dream, with hundreds of years spent in pursuit of independent…

Humanoid robots have been a long-lasting dream, with hundreds of years spent in pursuit of independent…

What are the best WordPress Security plugins and how to set them up the best way…

How to build a website with WordPress and what are the best plugins to use Building…

Cloud heavyweights AWS, Microsoft Azure, and Google Cloud Platform (GCP) are positioning themselves to use AI…

Web Real-Time Communication (WebRTC) has emerged as a powerful technology that enables direct browser-to-browser communication without…

Introduction Remote access is a cornerstone of modern IT infrastructure, enabling administrators and users to manage…

As a tech journalist, Zul focuses on topics including cloud computing, cybersecurity, and disruptive technology in…

If you are seeking to enhance your website’s reach and engagement on social media, you have…

NetApp, a data infrastructure company, has expanded its partnership with Google Cloud to make it…

What is Matrix? Matrix is an open protocol for decentralized, secure communications built on the principles…
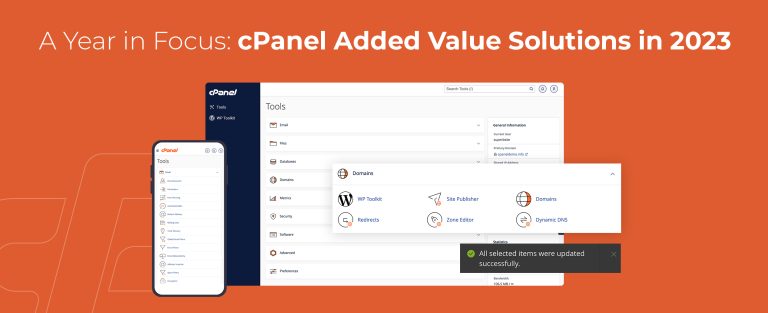
With the year slowly coming to an end, we draw the curtains on yet another chapter…

Implementing observability in cloud-native applications Cloud-native hosting technologies have taken centre stage ever since they were…

Software mapping is an important concept in the field of software engineering and cloud computing. It…

In this video, we’re bringing you the biggest cybersecurity stories of the week. 🥷 Check out…

Artificial intelligence (AI) and data science are revolutionizing customer service with advanced algorithms and cutting-edge generative…

This article will discuss the state of finding your current geographical location in the Fedora Linux…
#funfacts #fyp #cybernews If you find this video interesting, don’t forget to like, share, and subscribe…
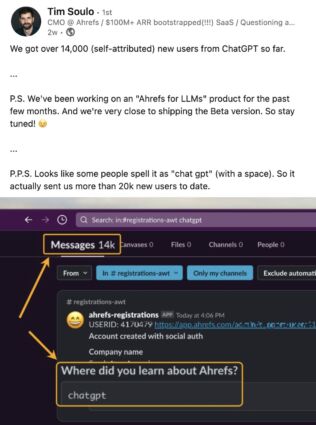
We studied the traffic of 3,000 websites to better understand the size and make-up of AI…

As AI is gaining traction, many cloud solutions are enhanced to better support AI use cases….

In this video, we’re bringing you the biggest cybersecurity stories of the week.🥷 Check out a…
So a we are a little bit into the new year I hope everybody had a…

Humanoid robots have been a long-lasting dream, with hundreds of years spent in pursuit of independent…

Virus notifications can be quite concerning, and they are definitely alarming for any Mac user, regardless…
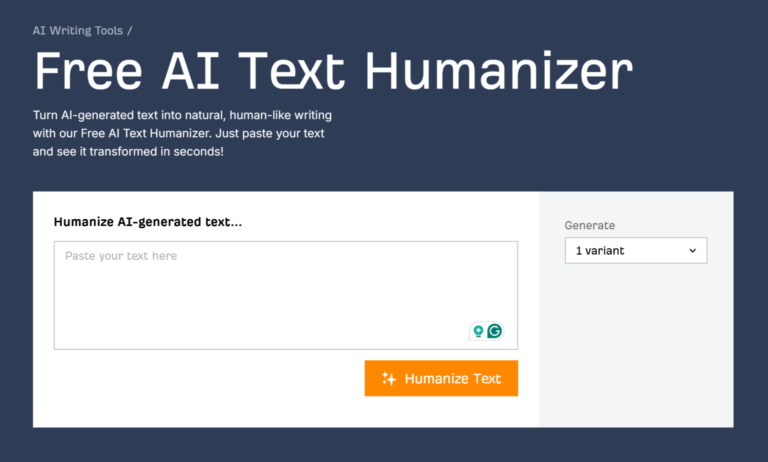
There are tons of tools promising that they can tell AI content from human content, but…

Introduction Debian-based Linux distributions, such as Ubuntu, Linux Mint, and Debian itself, rely on robust package…

Proper planning is the first step for a successful on-premises Exchange Server to Microsoft 365 migration….

In this video, we’re bringing you the biggest cybersecurity stories of the week.🥷 Check out a…

As the dust settles from the recent presidential elections, the future of data sovereignty continues to…

🔥 Get the best AI video generator with a discount! 🔥 ✅ Try Synthesia – best…

Introduction In the world of modern software development and IT infrastructure, containerization has emerged as a…

The EU’s Digital Operational Resilience Act (DORA) regulation came into full effect on January 17, 2025,…